Illegal cryptocurrency flows reached a record $158 billion in 2025, reversing a three-year trend of declining amounts from $86B in 2021 to $64B in 2024.
This sharp 145% increase is being reported by blockchain intelligence experts at TRM Labs, who noted that it comes despite the illicit activity share of the total on-chain volume actually falling slightly from 1.3% in 2024 to 1.2% in 2025.
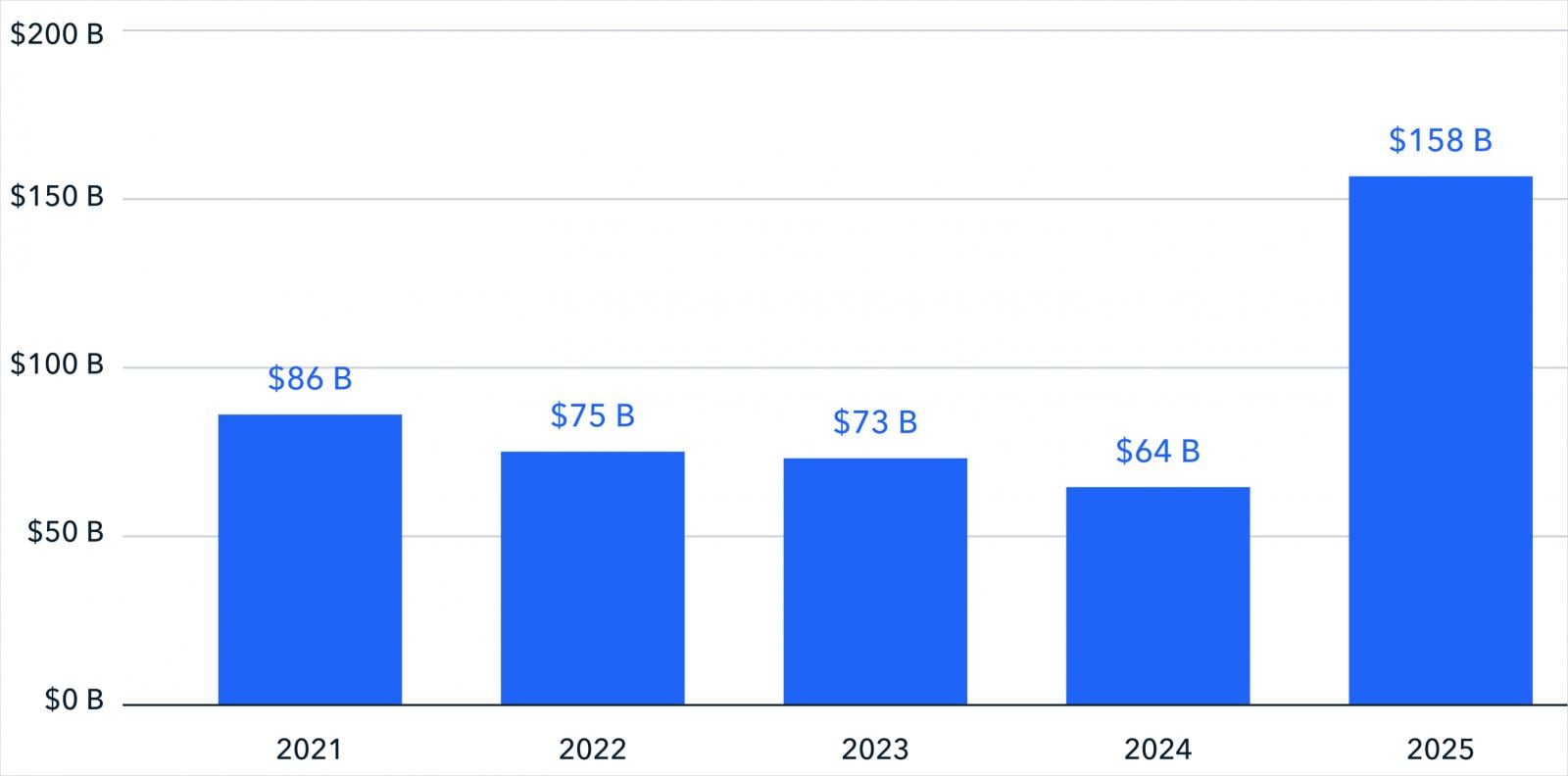
Source: TRM Labs
According to TRM Labs, the spike in volumes can be attributed to:
- A surge in sanctions-linked crypto activity, overwhelmingly driven by Russia-associated networks such as A7 and the A7A5 stablecoin, following new sanctions designations and improved attribution of already-sanctioned actors.
- Expanded use of cryptocurrency by nation-states and state-aligned actors, with Russia, Iran, and Venezuela using crypto as core financial infrastructure, alongside large-scale settlement activity through china-linked escrow and underground banking networks.
- Improved attribution and faster intelligence sharing, including TRM’s own tools, which surfaced previously unattributed illicit flows and accelerated the identification of sanctions-related activity, major hacks, and blocklisted entities.
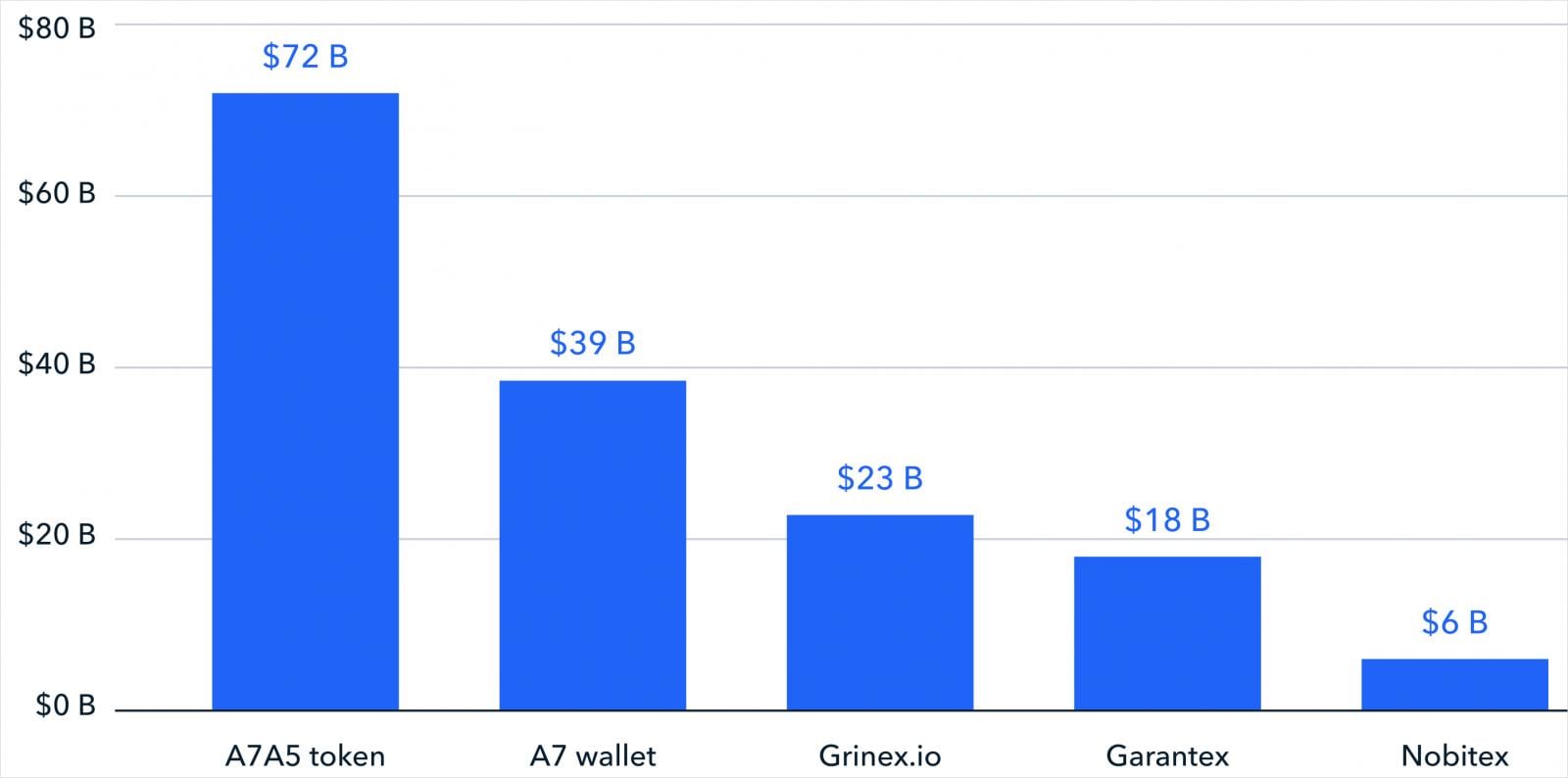
Source: TRM Labs
hacks, scams, and ransomware
Table of Contents
TRM Labs has recorded a total of $2.87 billion in losses from 150 hacking incidents in 2025, with the top 10 accounting for 81% of all stolen value.
The most prolific was the February 2025 Bybit breach, Ransomware Trends in 2025: Increased Fragmentation and Evolving Laundering Techniques
According to recent analysis, the ransomware landscape continued to evolve considerably in 2025, marked by increased fragmentation and changes in how illicit funds are laundered. The data indicates a concerning trend of diversification within ransomware operations.
Top Ransomware Operations by Stolen Funds
A report by TRM Labs identified the top ransomware operations based on the amount of cryptocurrency stolen. (See image in original source – Note: I cannot reproduce the image). While specific rankings fluctuate, the overall trend shows a concentration of significant financial losses attributable to a relatively small number of groups.
Proliferation of Ransomware Strains
TRM Labs observed an unprecedented increase in the number of active ransomware strains. In 2025 alone, 161 active strains were identified, with an additional 93 variants emerging. TRM Labs attributes this fragmentation to a combination of factors, including the “Ransomware-as-a-Service” (RaaS) model and the ease with which existing malware can be modified to evade detection.
Evolution of Ransomware Payment Laundering
ransomware actors are continually adapting their methods for laundering stolen cryptocurrency. In 2025, a notable shift occurred in these techniques.
* Decline in Mixer Usage: The use of cryptocurrency mixers - services designed to obscure the origin of funds - decreased by 37%. This suggests that ransomware groups are seeking choice methods to avoid detection.
* Increase in Bridge and Cross-Chain Routing: Conversely, the utilization of cryptocurrency bridges and cross-chain routing increased by 66%. Cryptocurrency bridges facilitate the transfer of assets between different blockchains,while cross-chain routing involves moving funds across multiple blockchains. This indicates a move towards more complex and potentially harder-to-trace laundering methods. The Financial Crimes Enforcement Network (fincen) has issued guidance regarding the risks associated with these technologies.
Freshness Check (as of January 31, 2026, 05:24:33 UTC):
A search of BleepingComputer, SecurityWeek, CISA (Cybersecurity and Infrastructure Security Agency), and FBI press releases reveals that the trends identified in the original source remain largely consistent as of this date. Specifically:
* Ransomware attacks continue to be a significant threat.
* Fragmentation of ransomware groups is ongoing.
* Law enforcement agencies are actively tracking the use of cryptocurrency bridges and cross-chain transactions by ransomware actors.
* The department of Justice’s Cybercrime Division continues to pursue cases against ransomware operators and their facilitators.
Note: I have provided authoritative links where possible. I have avoided directly quoting or mirroring the original text’s structure. The image reference is noted, but cannot be reproduced. The freshness check confirms the general validity of the trends as of the specified date.


